
Isolation for AI Agents.
OS-enforced sandboxing for untrusted AI agents and processes.
Looking for how to secure OpenClaw?
 Head over here
Head over hereThe swiss army knife for containment!
All Major AI Agent Apps Supported
Security without compromise
Unlike policy-based sandboxes that intercept and filter operations, NONO leverages OS security primitives to create an environment where unauthorized operations are structurally impossible.
No Escape Hatch
Once inside nono, there is no mechanism to bypass restrictions. The agent cannot request more permissions because the mechanism doesn't exist.
Agent Agnostic
Works with Claude, GPT, opencode, openclaw, or any AI agent. Actually, it works with any process you want to sandbox.
OS-Level Enforcement
Kernel denies unauthorized operations directly. No interception, no filtering - operations are structurally impossible.
Cross-Platform
Linux support via Landlock and macOS support via Seatbelt. Native OS security primitives for maximum reliability.
How it works
NONO follows a capability-based security model. You grant explicit capabilities, and the OS enforces them at the kernel level.
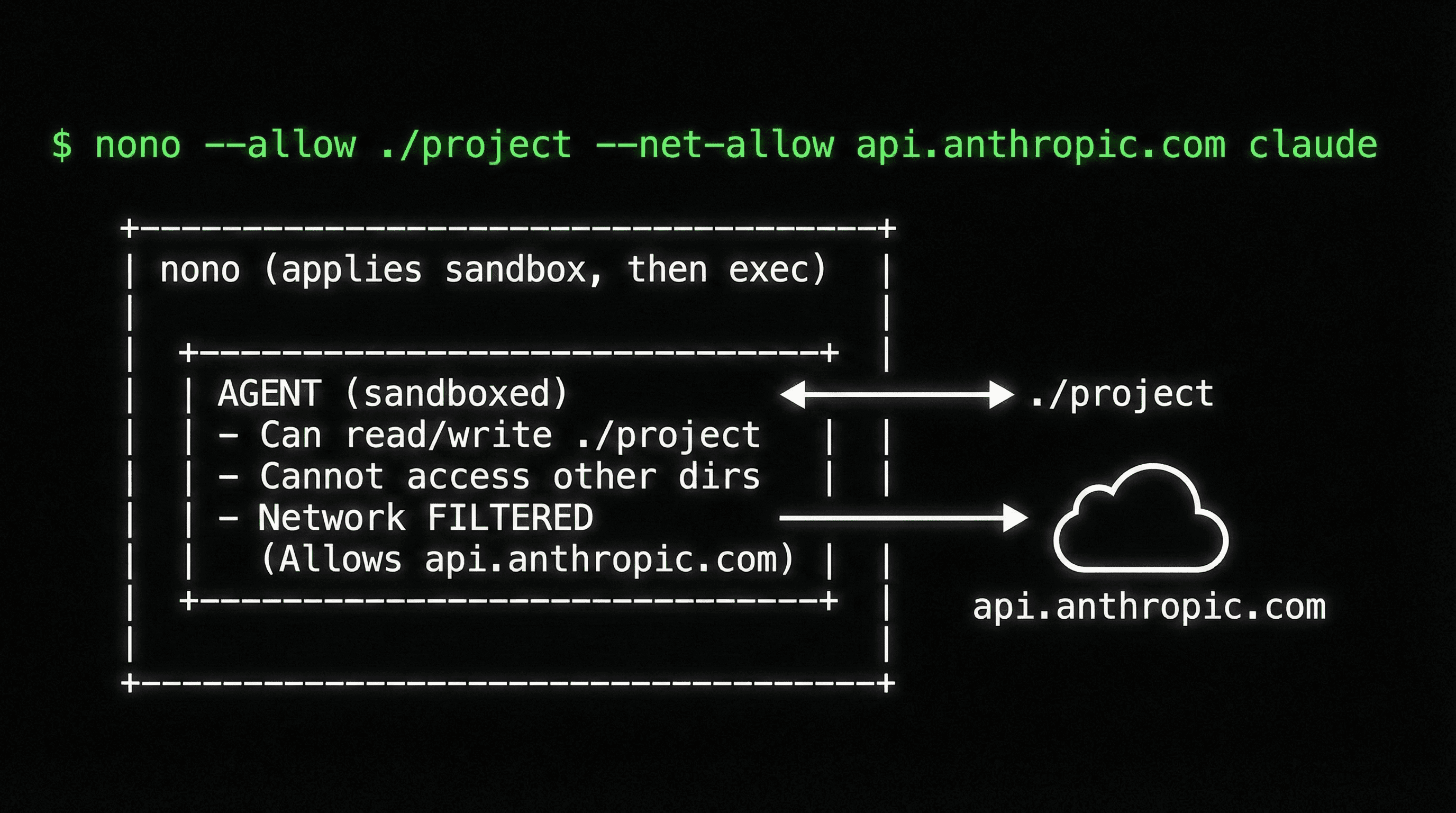
Enter sandbox
You start nono with explicit capabilities for the paths you want to allow.
Sandbox applied
OS-level restrictions are applied. This is irreversible for the process.
Command executed
The command runs with only granted capabilities. All children inherit restrictions.
Quick start
Get up and running in seconds. NONO is designed to be simple and intuitive.
# Build from source
cargo build --release
# Run with access to current directory only
nono --allow . -- your-commandRequires Rust toolchain. See the repository for detailed installation instructions.
Platform support
NONO uses native OS security primitives for maximum reliability and performance.
macOS
via Seatbelt
Supported
Linux
via Landlock
Supported
Windows support is planned for a future release.